OneRNG
OneRNG is an entropy source / hardware random number generator (HWRNG), designed to be connected via USB to your computer.Entropy is collected from an avalanche diode circuit and optionally an RF circuit, whitened and presented over a USB/Serial connection.
The provision of entropy to your computer system is critical for any software security system to be effective. There are many potential sources of entropy, but the majority of them are susceptible to biases & attacks that can result in the subversion of your privacy & security. Many of these attacks are undetectable in normal working conditions.
In order to address these problems, we present OneRNG. This is deliberately a simple device, which means that instead of having to blindly trust the hardware you are attaching to your computer, you have the ability to verify that the software and hardware of this device is to your standards.
We are not aware of any other equivalent device that promotes this essential feature of security for you, the user.
TL;DR - Shut up and take my money!
The V3 external and V2 internal OneRNG are currently for sale on the Moonbase Otago eshop. Sadly the programmer is not currently in stock.
Verify your security
Don't trust us; trust yourself
Many decisions in our lives are made by extending trust to other people, and this is an essential part of what makes the world work. Vendors have reputations, affected by news and reviews. Many of them have great reputations, and well-deserved.But there are more and more verified examples where the reputation of the original vendor is undermined by the actions of others; supply-chains are subverted, products are tampered with while being shipped, and so on.
When it comes to your own computer, there's a huge amount that you have to trust, that you cannot inspect. Many people are still using operating systems that do not disclose their own source code; even where the code is available many people do not verify that the binaries they are running have actually come from the claimed code. And then we have to start looking at the actual hardware, and wonder about the code running in the BIOS, on the connected devices (such as disk controllers), even the microcode on the CPU.
OneRNG can't address all those issues, but we can give you a source of random data that can be used as the basis of all your encryption. You can inspect this source, and verify that it is working exactly the way we have described. Any tampering with the device before you get it should be detectable - hardware or software.
You don't need to trust us to provide this essential cornerstone of security - you can verify OneRNG for yourself.
Open Source :




First, the design and software of the OneRNG is completely open. This means that the hardware layout is fully published, and that the software used on the device is available to you in source form. We achieve this by releasing the sources under the GNU GPLv3 and LGPLv3 licenses, in accordance with the Open Source Hardware Association community definition. OneRNG is now fully OSHWA certified, with UID NZ000001.
Physical inspection
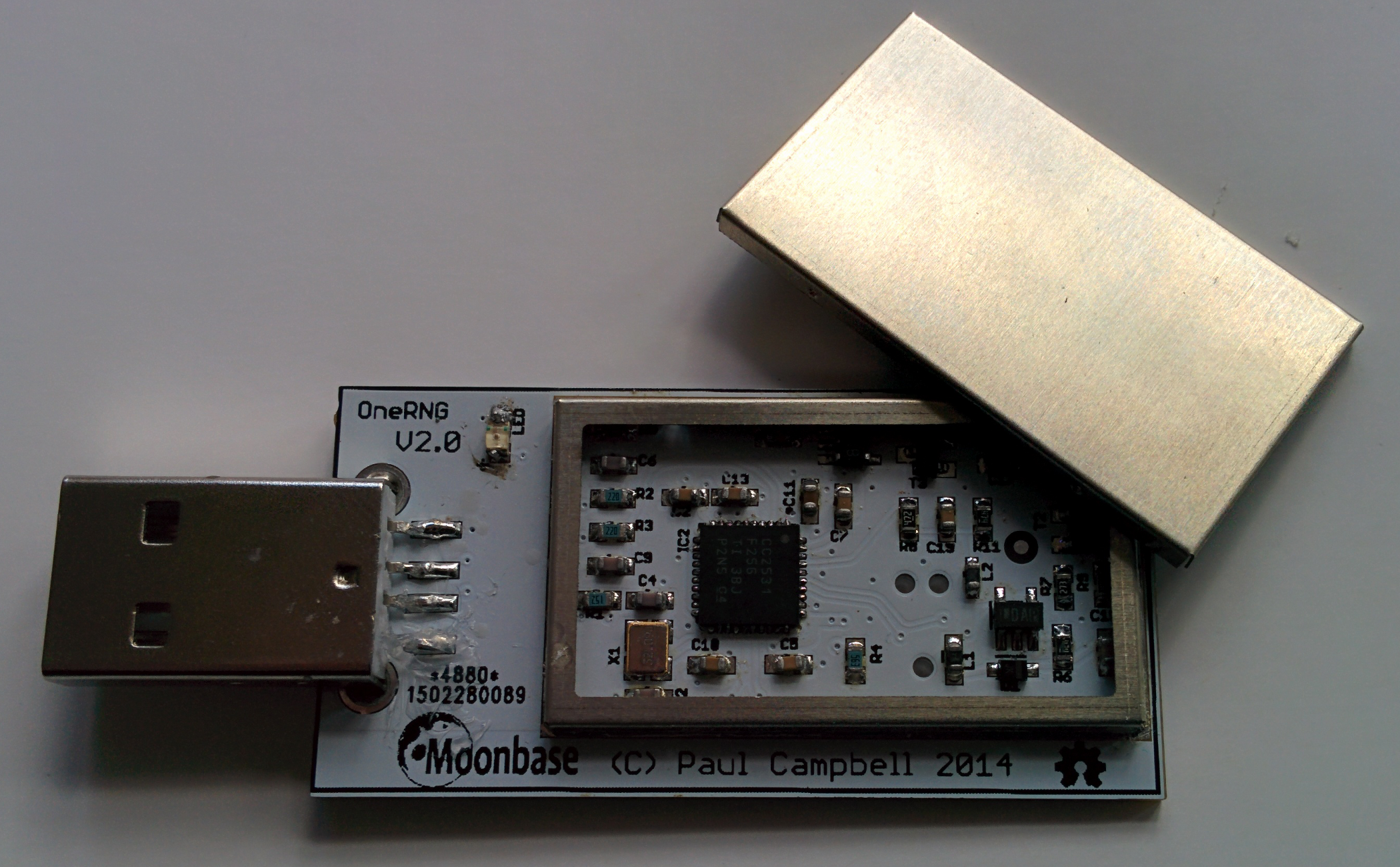
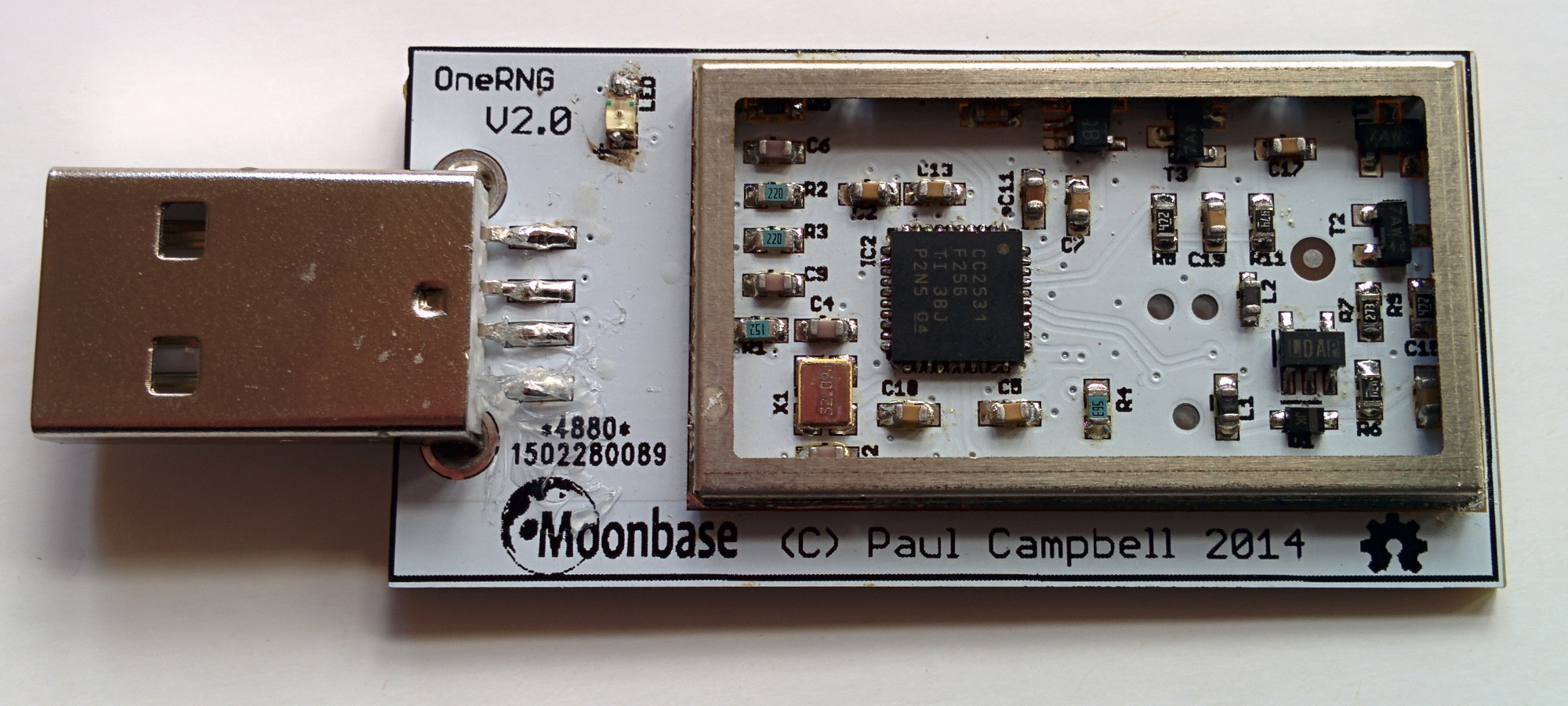
Second, uniquely amongst such devices, we deliberately construct the OneRNG to be physically big enough to be inspected by eye. You can remove the "tin foil hat" shield from the device (please put it back on before plugging it in though), and confirm that the board layout really does match the design.Far too many devices make their hardware too small to easily inspect, with essential connections hidden inside or underneath other components. Some even cover sections of their boards with opaque resin, which seems to do a great job of preventing post-delivery tampering, but prevents the end-user from doing their own inspection of the device.
Component ubiquity
There is one complex chip on the OneRNG which cannot be verified by eye. The CC2531 SoC (from Texas Instruments) is small, and it is theoretically possible that the chip fitted to your device has been tampered with or even been outright substituted for an alternative before you received your device.However, the CC2531 is cheap, ubiquitous, and found in a huge range of consumer electronics around the world. If you want to address the risk that your device has been subverted, just buy any consumer device also using this chip, preferably second-hand, and swap the chips over.
If you need to entertain the possibility that all CC2531 chips ever produced have been compromised, we can help you there as well. The most likely component on the chip to have been 'backdoored' (and to never have been detected) is the AES module. Our software does not use this module at all; instead we use our own code to provide (albeit a bit more slowly) the equivalent functions.
Integrate with your OS
While you can talk directly to the OneRNG with a simple serial connection, we expect that most users will want to use it to feed entropy into your Operating System's existing RNG facilities, improving the quality of the all random numbers used by your computer.Even if you have untrusted entropy sources in your machine, mixing the verifiable OneRNG into your random number generator will mitigate weaknesses or attack vectors from the other sources.
Protected from software exploitation
Many USB-connected devices are reprogrammable over their USB interface, which means you can never be sure that the firmware on the device is doing what you want it to do (q.v. BadUSB)The OneRNG default firmware does not allow itself to be reprogrammed over the USB bus; instead you need to connect a dedicated programmer unit (available separately, licensed in the same way as OneRNG itself).
Of course, if you want to reprogram the firmware yourself to permit USB-reprogramming, because that suits your environment, that's completely fine. That's what Open Source software and hardware is all about.
Verify the software as well as the hardware
The firmware for OneRNG is actually pretty small, compared to the 256KB of storage available on the CC2531. In order to be confident that the firmware on your unit is the one we intended it to be, we padded the firmware image out with random data up to almost 256KB, and digitally signed it. That signature can be verified by you, and indeed our default OS tools check the complete 256KB image against the signature every time the device is plugged in.Of course, if you want to put your own firmware image on the device, that will over-write or otherwise invalidate the signature.
Buy it now
The V3 external and V2 internal OneRNG are currently for sale on the Moonbase Otago eshop. Unfortunately, the programmer is not available at the moment.
More Information
- Where can I get a OneRNG from? — The Moonbase Otago eshop is now taking orders
- What is OneRNG? — Technical details
- I have a OneRNG — How can I verify and use my unit?
- I have a OneRNG programmer — How can I verify and use my unit?
- OneRNG Discussion Group — email list
- Presentations, Reviews & Awards
- The OneRNG story — Who runs the OneRNG project?